Which of the Following Are Not Consequences of Phishing
I find that emails that adopt an. Which of the following are warning signs of mortgage fraud.

How To Spot A Phish Infographic Phishme Cyber Security Awareness Cyber Security Education Infographic
Some common best-practices that should be used regardless of presence of any specialized phishing protection software include Avoid using open public networks.

. Even for cautious users its sometimes difficult to detect a phishing attack. It is usually carried out through spoofed emails and spoofed websites that urgently ask for various types of information. Phishing is an example of social engineering.
Attackers send out thousands of emails with the intent of getting the recipients either to respond to the email with personal information or to get the recipient to click a link. A collection of techniques that scam artists use to manipulate human psychology. Misdemeanor fines typically do not exceed a couple of thousand dollars while felony fines can be as much as 10000 or more per offense.
Phishing is a form of cyber fraud that attempts to get its victims to part with something of value such as money or personal information through deceptive emails or other electronic communications. Phishing is a common prelude to a ransomware attack. There are many potential consequences and identity theft is among the very worst of them.
One of these avenues of criminal behaviour is called Phishing. Data sent over public. The intent is often to get users to reveal financial information system credentials or other sensitive data.
If the phishing activity resulted in a victim losing money the court will impose a restitution order. Phishing is but a modern twist to any number of age-old ploys to trick people into giving up information that can be used against them. If you got a phishing email or text message report it.
You can mitigate the adverse effects of having your data encrypted in a ransomware attack by maintaining a current backup. Spear phishing involves attackers using emails file sharing and internet browsing of target users to gather information which then leads to a targeted attack. Requests to sign blank forms c.
The information you give can help fight the scammers. Being convicted of a phishing crime can also lead to a significant fine. Claiming that you must update or validate information.
These attacks become more sophisticated over time and hackers find ways to tailor their scams and give very convincing messages. Phishing is an attack tactic using email. Consequences of Mortgage Fraud Cognitive Domain.
Phishing refers to the act of obtaining victims sensitive information by posing as trusted companies and organizations. That number is only an average and can be much higher depending upon the type and volume of sensitive data that is lost or stolen. If you fall victim to a credit card phishing scam the perpetrators can gain access to your credit card numbers and a lot of other personal information.
If you got a phishing text message forward it to SPAM 7726. Directing you to a web site that is real. In 2016 alone attackers used phishing hacking malware and other strategies to steal 42 billion records from organizations.
How To Prevent Phishing. Of the following which is not a characteristic of a phishing attempt. Furthermore 81 of organizations that were attacked lost customers.
Learn more about the basics of credit card phishing scams by checking out the following information. Phishing tricks victims into giving over credentials for all sorts of sensitive accounts such as email corporate intranets and more. Phishing is the exploitation of any weaknesses whether technologically or in humans to gather personal andor sensitive information from an individual or organization for fraudulent activities.
Claiming to be from military service government organization or other plausible sender. Effectively preventing these attacks would require monitoring all these activities and in many cases in real-time. Phishing is a type of social engineering where an attacker sends a fraudulent eg spoofed fake or otherwise deceptive message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious software on the victims infrastructure like ransomwarePhishing attacks have become increasingly sophisticated and often transparently.
Tip 15 Investing in the right technology. Clone Phishing is where a legitimate and previously delivered bit of online correspondence is used to create an almost identical or cloned email. Over a 12-month period world-wide there were 62 billion attempted attacks to businesses and organisation online.
The consequences to a company its employees and its customers can. Increased commissions for brokers and appraisers d. In the case of a phishing scam targeted at a business the average breach costs an organization 386 million according to IBM.
Phishers will often send you e-mails asking that you update or validate information. Its a tactic used very often so security professionals need to be aware of phishing and some of the common tactics. As users become wiser to traditional phishing scams some fraudsters are abandoning the idea of baiting their victims entirely.
Which of the following are NOT consequences of phishing. Phishing is when attackers send malicious emails designed to trick people into falling for a scam. Some indicators of a phishing attempt would be formatting or spelling errors in an email an email sent by a company with which you do not have an account and if the email.
Phishing attacks can be categorised into three main forms those with an authoritative tone those that prey on greed and those with an opportunistic message. They can use your credit card to go on shopping sprees and. The best way to recognize a phishing attempt is to call the number provided to you in a suspicious e-mail.
All of the above answers are correct Ans. The attacks are performed by impersonating a trusted entity usually via email telephone vishing or private messages smishing. Phishing prevention is rarely a single course of action and is best implemented using a combination of common sense and certain specialized software.
Always backup your data. Phishing attacks were responsible for as much as 73 of malware being delivered to organisations world-wide in only a 12month period. The cloned communication will include malicious links or attachments which will likely be trusted by the victim due to the previous email communications.
This order requires you to pay the victim to. Users can help defend against smishing attacks by researching unknown phone numbers and by calling the company named in suspicious SMS messages if they have any doubts. How To Report Phishing.

Security Awareness Poster Used To Educate People On How To Recognize Fake Emails And Ph Cyber Security Education Information Technology Humor Computer Security
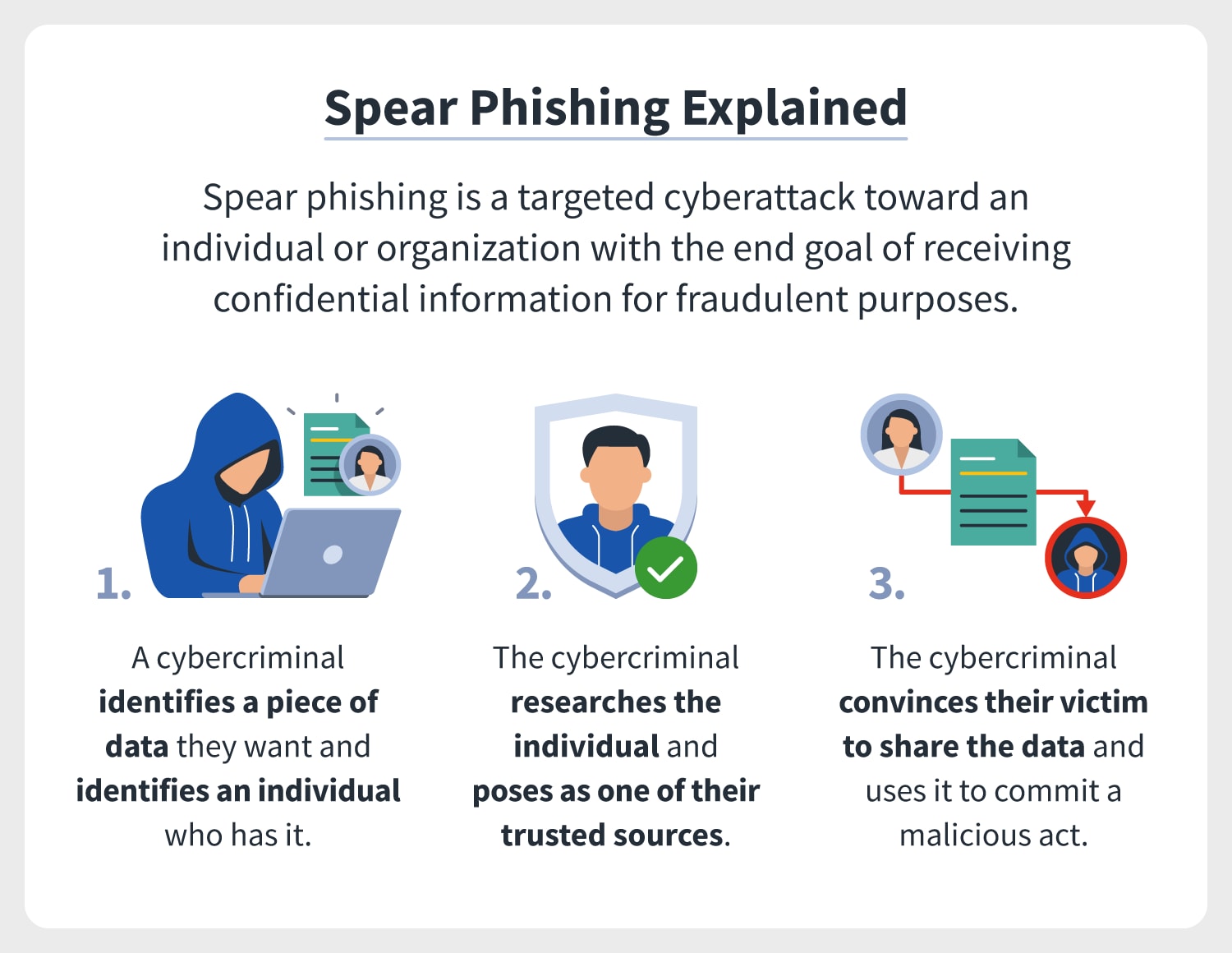
Spear Phishing A Definition Plus Differences Between Phishing And Spear Phishing Norton

No comments for "Which of the Following Are Not Consequences of Phishing"
Post a Comment